HTTP proxies and traffic analysers
Burp Suite
Burp Suite is an HTTP proxy, developed by PortSwigger. There is a private and a free version. The free version lacks the scanner, and the private version is very expensive. Even with the missing scanner, as a proxy it is the basic tool for web application pentesting and bug bounty hunting.
Proxy
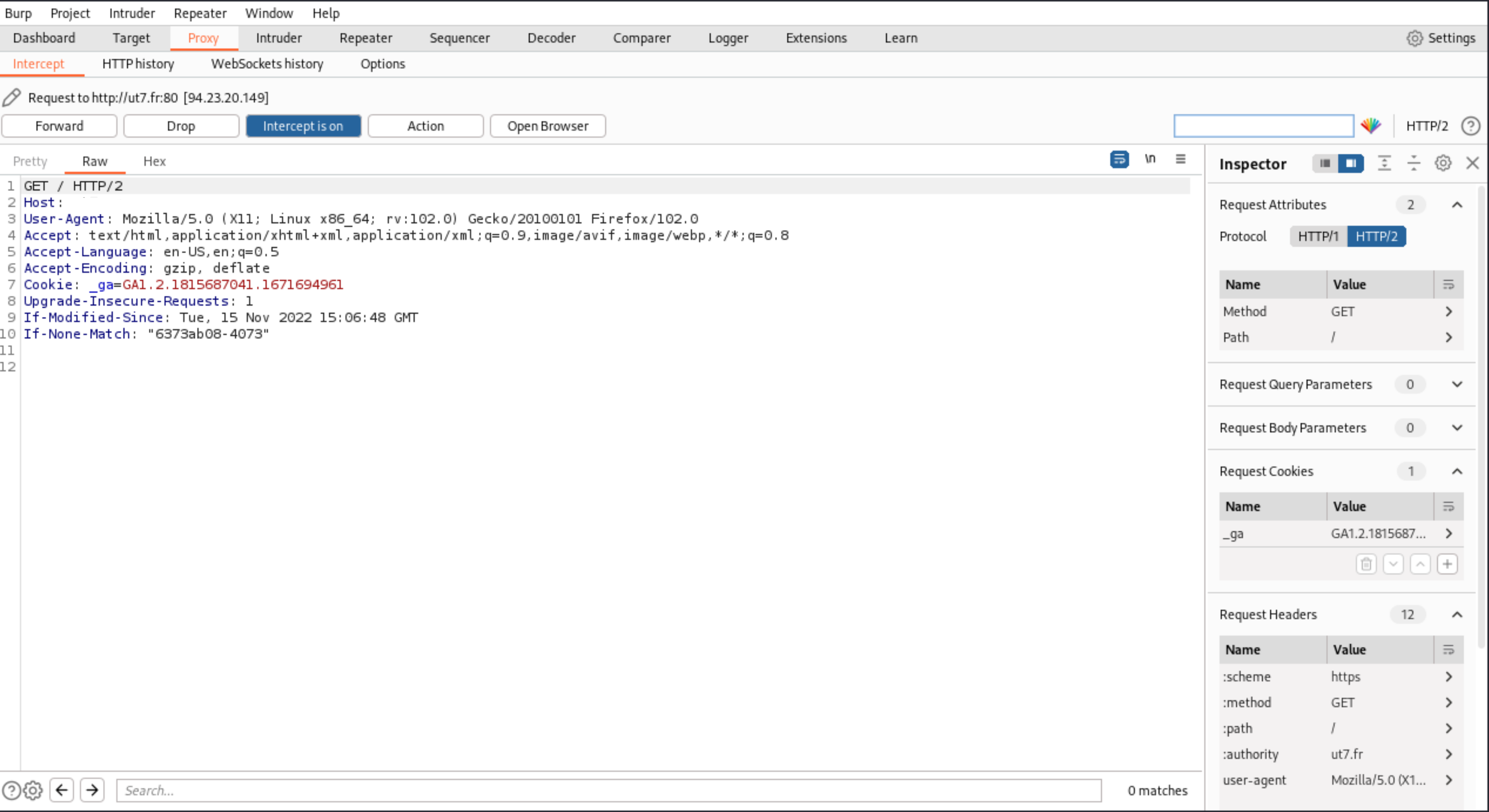
If you go to the Proxy tab, you will see four buttons (Forward, Drop, Intercept is on, and Action), to control the requests: send and receive.
 |
|---|
With Forward, Drop, Intercept is on, and Action, you can catch a request from your webbrowser, analyse the content, modify it, and send it to the application. |
These are the most basic options, and the most frequently used buttons in any HTTP proxy. Burp can do more.
Intruder
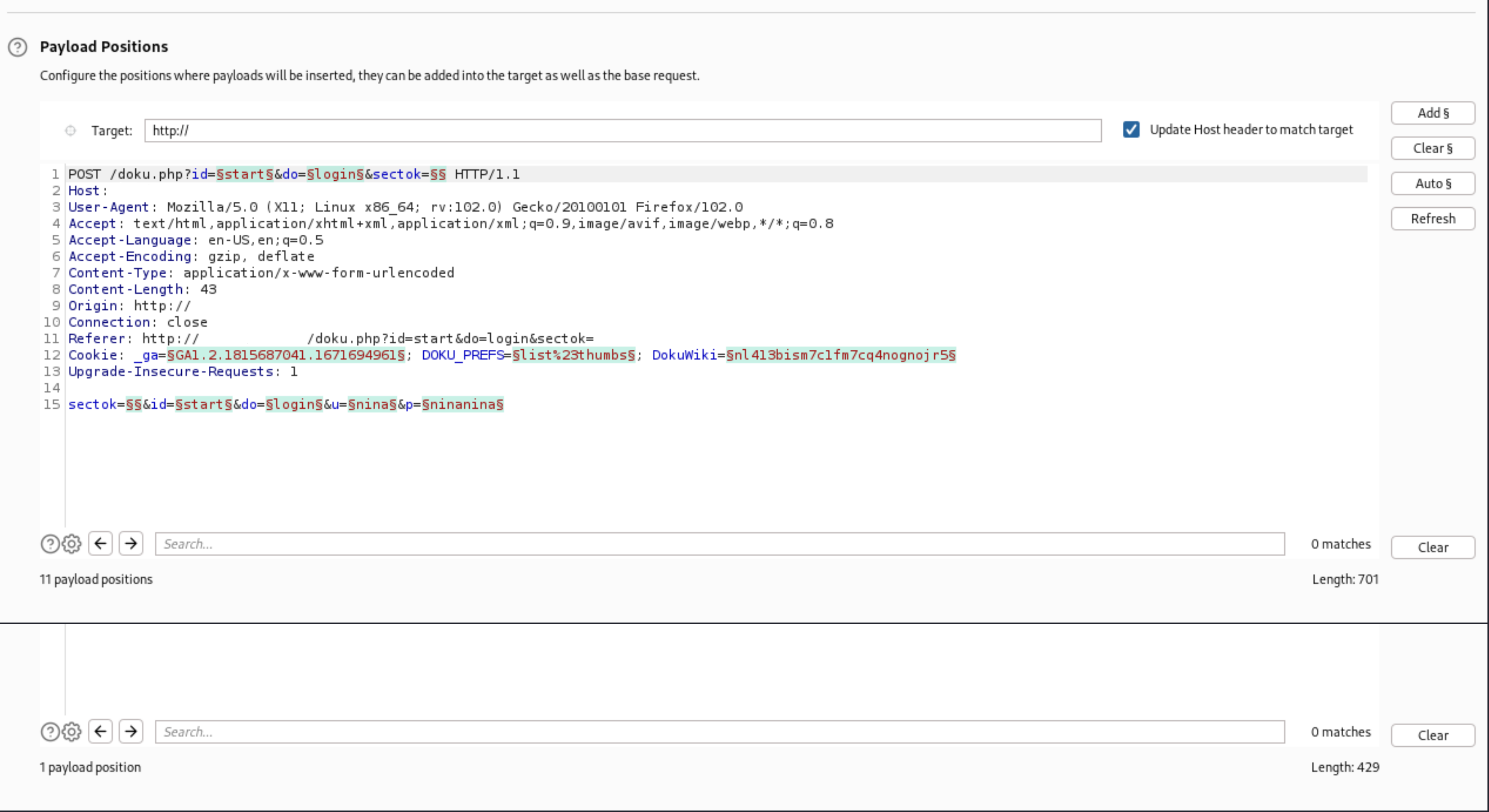
The Intruder tab offers a tool that automates the sending of modified requests. This tool makes it possible to send a large number of requests with testing strings, lists of numbers, and real values.
 |
|---|
| You can choose how the tool inserts the different values and where. |
 |
|---|
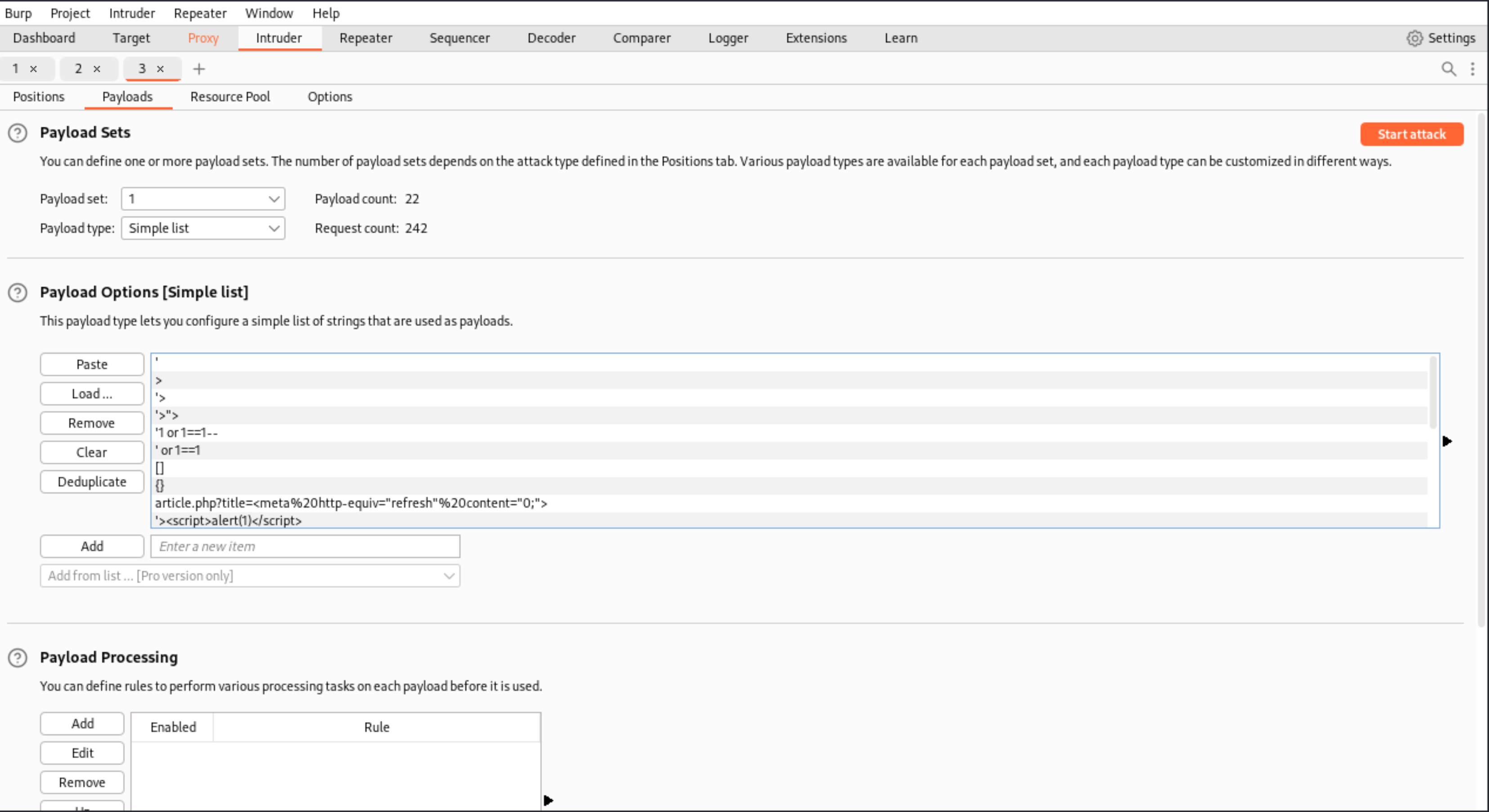
| ** Create a list with all the different types of testing strings to load in Intruder**. |
Then you can analyse the responses, looking for specific behaviours that could signal a vulnerability.
Repeater
 |
|---|
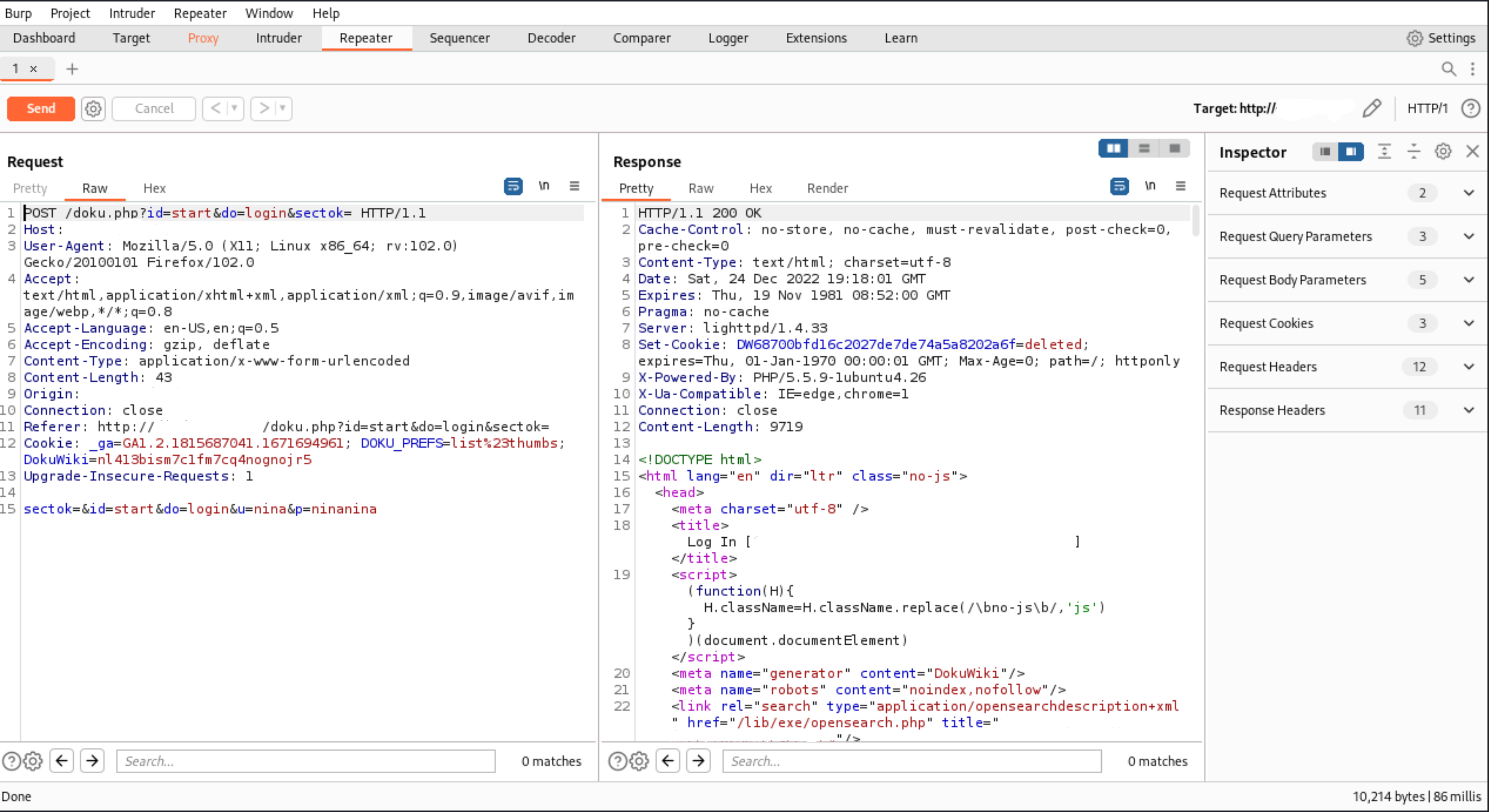
| Burp's Repeater can be useful when interacting with the application's backend, modifying a certain request. |
Extensions
Extensions can be found in the Burp app store and can be added just like a JAR file. Most of them are free.
The tool is awesome. But like said, the scanner is only available in the paid version which is expensive.
Zap
ZAP evolved from Paro, and was developed by the OWASP project. It is very similar to Burp Suite and has a proxy, and tools such as a repeater, intruder, fuzzer, and a vulnerability analysis tool.
Fiddler
Fiddler is another HTTP proxy, and is more targeted at .NET developers. It does not have the assessment options like Burp or Zap, but is useful when analysing applications developed in .NET, where the binary format is difficult to understand by other proxies.
Wireshark
During web application security assessments, it is not very common to analyse network traffic. And sometimes there are applications that use some components not running on the common 80 or 443 ports, and open other ports and services.
In this context, we can use it to analyse traffic between localhost and the internet, to understand a specific behaviour.
Use flows to limit the scope. Create a filter by hostname, otherwise you will get flooded with other packets that are not part of the specific connection you are checking. To make host name filters work, enable DNS resolution in settings: Go to menu View -> Name Resolution, and enable the necessary options Resolve * Addresses. Look for the hostname and create a filter from it.
Firebug
Firebug is a Firefox extension commonly used by developers to detect errors during the execution of web applications. But it can also be used to assess applications and understand abnormal behaviours. Firebug is included in Firefox’s Developer edition by default.
Installing Firefox’s Developer edition
Download the
firefox*.tar.bz2file from Mozilla’s website.Open Terminal and navigate to the folder where the file is saved.
Copy
firefox*.tar.bz2file to the/optfolder.
sudo cp -rp firefox*.tar.bz2 /opt
Delete the downloaded
firefox*.tar.bz2file.
sudo rm -rf firefox*.tar.bz2
Navigate to the
/optdirectory.Un-tar the
firefox*.tar.bz2file.
sudo tar xjf firefox*.tar.bz2
Delete the
firefox*.tar.bz2file.
sudo rm -rf firefox*.tar.bz2
Change ownership of the folder containing Firefox Developer Edition
/opt/firefox:
sudo chown -R $USER /opt/firefox
Create the shortcut:
nano ~/.local/share/applications/firefox_dev.desktop
Content:
[Desktop Entry]
Name=Firefox Developer
GenericName=Firefox Developer Edition
Exec=/opt/firefox/firefox %u
Terminal=false
Icon=/opt/firefox/browser/chrome/icons/default/default128.png
Type=Application
Categories=Application;Network;X-Developer;
Comment=Firefox Developer Edition Web Browser.
StartupWMClass=Firefox Developer Edition
Mark the launcher as trusted and make it executable.
chmod +x ~/.local/share/applications/firefox_dev.desktop
To access Firebug, right-click on a website and select
Inspect Element.